The era of targeted ransomware: attacks on high-profile victims grows nearly eightfold from 2019 to 2020
From 2019 to 2020, the number of Kaspersky users encountering targeted ransomware—malware used to extort money from high-profile targets, such as corporations, government agencies, and municipal organizations—increased by 767%.
From 2019 to 2020, the number of Kaspersky users encountering targeted ransomware—malware used to extort money from high-profile targets, such as corporations, government agencies, and municipal organizations—increased by 767%. This increase in targeted ransomware occurred alongside a 29% decrease in the overall number of users affected by any kind of ransomware, with WannaCry still the most frequently encountered family. These are among the most important findings in Kaspersky’s recent report on the ransomware landscape from 2019-2020.
The ransomware threat—when attackers encrypt private information and hold it ransom—became mainstream news in the 2010s following large-scale outbreaks, such as WannaCry and Cryptolocker. They targeted tens of thousands of users and often requested relatively small amounts from victims to have their files returned. Over the years, these campaigns have been on the decline. In fact, from 2019 to 2020, the total number of users that encountered ransomware across all platforms declined from 1,537,465 to 1,091,454—a decrease of 29%. Alongside this decline, however, there has been a rise in targeted ransomware.
Targeted ransomware attacks—attacks against a chosen victim with the goal of extorting money—are often aimed at high-profile targets, such as corporations, government and municipal agencies, and healthcare organizations. The attacks involve significantly more sophistication (network compromise, reconnaissance and persistence, or lateral movement) and a much larger payout.
From 2019 to 2020, the number of users encountering targeted ransomware increased by around 767%.
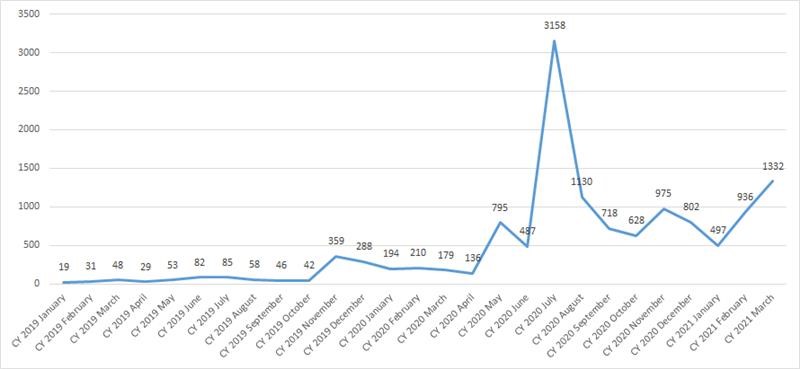
The number of unique Kaspersky users affected by targeted ransomware, 2019-2020
Some of the most prolific targeted ransomware families during this time were Maze, the infamous group involved in several high-profile incidents, and RagnarLocker, also covered in the news. Both of these families began the trend of exfiltrating data in addition to encrypting it and threatening to make the confidential information public if the victims refused to pay. WastedLocker also made front-page headlines with similar incidents. In many of these cases, the malware is specifically designed to infect each individual target.
Despite the rise in targeted ransomware, the ransomware family most frequently encountered by users is still WannaCry, the ransomware Trojan that first appeared in 2017 and led to damages of at least $4 billion across 150 countries. Nearly 22% of the users that encountered ransomware in 2019 encountered WannaCry; this decreased to 16% in 2020.
“The ransomware landscape has fundamentally changed since it first became big news in the security community. We’ll most likely see fewer and fewer widespread campaigns targeting everyday users. Of course, that’s not to say users aren’t still vulnerable. However, the primary focus will likely continue to be on companies and large organizations, and that means ransomware attacks will continue to become more sophisticated and more destructive. It’s imperative that businesses adopt a holistic, comprehensive set of security practices to protect their data,” comments Fedor Sinitsyn, security expert at Kaspersky.
Read more about the ransomware landscape on Securelist.
To protect your company from ransomware, Kaspersky experts recommend that you:
- Always keep software updated on all the devices you use to prevent ransomware from exploiting vulnerabilities.
- Focus your defense strategy on detecting lateral movements and data exfiltration to the internet. Pay special attention to outgoing traffic to detect cybercriminal connections.
- Back up data regularly. Make sure you can quickly access it in an emergency when needed.
- Carry out a cybersecurity audit of your networks and remediate any weaknesses discovered in the perimeter or inside the network.
- Explain to all employees that ransomware can easily target them through a phishing email, a shady website or cracked software downloaded from unofficial sources. Ensure staff remain vigilant at all times and check their knowledge with tests.
- Along with proper endpoint protection, dedicated services can help against high-profile ransomware attacks. Kaspersky Managed Detection and Response proactively hunts for attacks and help to prevent them on early stages, before attackers reach their final goals.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
The era of targeted ransomware: attacks on high-profile victims grows nearly eightfold from 2019 to 2020
Kaspersky
Related Articles Press Releases
Kaspersky identifies BlindEagle’s new spy plugin
The BlindEagle APT (Advanced Persistent Threat) group has introduced several updates in one of their latest espionage campaigns targeting individuals and organizations from Colombia, the Kaspersky Global Research and Analysis team (GReAT) has reported. The updates include a new espionage plugin and the use of legitimate Brazilian file-hosting sites during the infection process. The group is increasingly leaving artifacts in Portuguese in their malicious code, whereas previously, they predominantly used Spanish. Kaspersky also observed BlindEagle launching a separate campaign that employs the DLL sideloading technique, uncharacteristic of the actor.Read More >Kaspersky discovers 'Tusk,' active information and crypto stealing campaign
Kaspersky has detected an online fraud campaign aimed at stealing cryptocurrency and sensitive information by exploiting popular topics such as web3, crypto, AI, online gaming, and beyond. Targeting individuals worldwide, the campaign is believed to be orchestrated by Russian-speaking cybercriminals and spreads info-stealing and clipper malware.Read More >Surprising digital privacy contradictions: 49% of users cover webcams, 40% rely on Incognito mode
A new study by Kaspersky has shed light on key digital myths and superstitions and consumers' attitudes towards themRead More >
We use cookies to make your experience of our websites better. By using and further navigating this website you accept this. Detailed information about the use of cookies on this website is available by clicking on more information.